Users and Access Controls
VC/m is designed so that it can be configured to be used by any number of users. A VC/m environment may be utilized by anywhere between one person, to hundreds working within a large and multi-layered organization. As such, VC/m incorporates User IDs and Access Rights.
Users IDs
Each user of the VC/m system should have their own unique User ID. A User ID is assigned a series of Access Rights (see below) and this in turn determines what the actions which that user may perform, as well as the information to which they have access.
Unless integrated with another security infrastructure, when connecting to the VC/m browser interface the user is prompted for their User ID and password with this dialog:
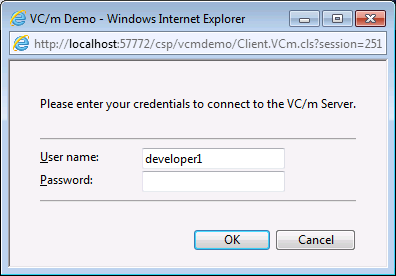
If VC/m is installed on Windows 2000 or later, UNIX/Linux or OpenVMS, VC/m checks the account name which has been used to log onto the operating system.
Access Rights
Access rights determine how a user may interact with the VC/m environment. Access rights work in the following way:
- They are defined in the list of access rights under Setup -> Access Rights.
- They are assigned to User IDs.
- They are applied to various elements of the VC/m environment, such as transfer routes, menus and location classes.
For example, when a user initiates the transfer of an object along a particular transfer route, the system compares the list of access rights applied to that transfer route with the list of access rights assigned to the user's ID. The system can then determine whether or not to validate the transfer.
See Also: Managing Users and Access Controls